Alright, back to the technical stuff. Well, sort of.
Something that’s been new to me is working remotely for a company where many of my coworkers are in different time zones. Although I was fully remote at SJU for the last few years of my time there, everyone I worked with started and ended their day at around the same time. That doesn’t happen when you’re working for a global company! To have a work / life balance these days, I need to be mindful of my own schedule. Here’s how I’ve used technology to help me do that.
July 2024: I’m updating this post without making a new one, just to keep things simple. Below each section, I’ve added some additional tips that I’ve learned since originally publishing this blog post.
Focus
macOS Ventura, iOS 16, and iPadOS 16 arrived at exactly the right time for me. I had just started at DoorDash, and was already familiar with Do Not Disturb mode and using the Health app to set a sleep schedule. I’m really glad Apple gave this feature so much attention with the Fall 2022 releases.
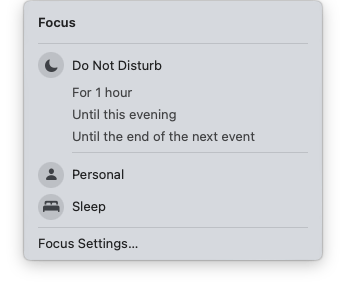
To get started, Apple has excellent documentation for iOS / iPadOS and macOS. You have a lot of flexibility to create different Focus modes, but I’ve settled on four: Sleep, Do Not Disturb, Personal, and Off. I work from 10 AM until 6 PM Monday through Friday, so I’ve built my Focus modes around those times.
Sleep: Sleep is a good place to start, since it has to be set up in the Health app on your iPhone. Pick what time you want to go to sleep, and what time you want to wake up. On the weekends, I give myself a slightly later bedtime, and a later wake time. You can pick an alarm if you want to, but I rely on our bedroom Sonos speaker for that, instead, so I can wake up to music. 😄
I’d recommend setting “wind down” to 0 minutes. It just activates Sleep focus early, which is somewhat unnecessary.
In Settings > Focus > Sleep, you can customize a number of things. For me, Sleep focus is my most restrictive – I have a custom Lock Screen (I’m using “Astronomy” which looks great at night), and the brightness is significantly dimmed. I only allow some apps to send push notifications – mostly ones like 1Password, in case I need an MFA code. I also made a page of apps solely comprised of ones that I’d need if I woke up at night or was getting ready for bed. I also have some shortcuts for actions such as the “good night” scene in Home or to quickly make a new to-do item in OmniFocus. I filter out my work email, too. Lastly, all badges are disabled.





Do Not Disturb: I want this to activate at 10 PM on weeknights, and 11 PM on weekends, well ahead of my actual bedtime. The end time doesn’t matter, since Sleep focus will take over. This is my own “wind down” time, where all notifications are silenced (again, except for apps like 1Password). I have a custom Lock Screen here too, so I can tell at a glance that I’ve activated Do Not Disturb. I picked an excellent wallpaper from Wallaroo and set it to greyscale, taking a colorful beach scene and turning it into a snowy evening. I also filter out my work email here, so I only see my personal email.



Personal: For obvious reasons, this is my favorite. I have a custom Lock Screen with a picture of my wife. It activates at 6 PM each weekday, but also in the mornings – my wake up time is at 9 AM, so it also covers from 9 AM until 10 AM (so I’m not hit with work emails as soon as I get out of bed).


Off: This is what’s in place during my work hours. “Off” is simply no focus activated – the default behavior for an iPhone. Since I manage Macs, I have an Apple-themed Lock Screen and Home Screen. All email accounts are shown in a unified inbox, and no notifications are silenced. I experimented with creating a “Work” focus, but for my purposes, it was kind of overkill to create a separate focus just for that.

Outside of those schedules, I’ll frequently toggle Do Not Disturb during the work day if I’m joining a Zoom call and don’t want to be distracted by notifications. When I’m on vacation, I manually toggle Personal on, so I don’t see any work emails. I used to fully remove my work account from my phone while on vacation, but this is significantly easier!
One of the best additions to macOS Ventura is that you can add a menu bar icon for Focus mode, allowing you to quickly switch to a different mode. All of your iCloud-connected devices will instantly adopt the same mode.
July 2024: Also, while you’re configuring notifications, disable your email “ding” noise. It’s more disruptive than you probably think. I leave the notification banners in place, but the noise pulls me out of flow unnecessarily.
Slack
Slack has an excellent guide to configuring notifications. I set my work hours in there, so I don’t receive any notifications in my off-hours. Coworkers can still push DM notifications through if it’s an emergency, but otherwise, it’s all silenced at the end of the day.

One additional consideration: since I have both my work Slack and the Mac Admins Slack on my phone, I found that I was still seeing badge notifications for DMs on my work Slack, even in my off-hours. This became hard to ignore, so my solution was to disable badges for Slack on iOS altogether. For similar reasons, I don’t have my work Slack on my home computer, as I found myself checking work notifications in my off-hours just to clear the badge.
July 2024: My colleague, Sam Keeley, offered an even better suggestion: install the Slack EMM app for my work Slack instance, and use the standard Slack app for the Mac Admins Slack. He also suggested removing the home icon for Slack EMM, but leaving the app installed, so I can open it via notifications (or Spotlight).
This also gives me the flexibility of blocking work Slack notifications with Focus mode, which has been great for when I stop for lunch and temporarily switch back to Personal focus.
Same as the mail “ding” noise, I’ve also disabled all of Slack’s notification sounds (except for incoming calls via huddles).
You can set your work hours in Google Calendar, too. My main recommendation here is to pad the time – in my case, I set my work hours from 10:30 AM to 5:30 PM. That gives me 30 minutes at the start of the day to catch up, as well as 30 minutes at the end of my day to wind things down.

Note that I’m not signed into my work email on my personal computer, and I’m not signed into my personal email on my work computer. However, I am signed into all of my calendars on both computers and my phone – this prevents me from double-booking events and makes it easy to block time on my work calendar as necessary.
July 2024: I’ve found it important to also schedule regular “meetings” for lunch and regular breaks. I shouldn’t be sitting for more than two hours at a time, so I’ve got items on my calendar (which can be moved if necessary) so I’m not scheduled in back-to-back meetings all day.
Smart Home
I’m extremely lucky to have my own home office – that was one of the reasons we bought our house in the first place. Even though that’s where I work from during the day, it’s also where I keep my personal computer and video game systems. I typically spend a lot of non-work time in my home office.
We picked up some Nanoleaf Shapes LED panels on sale a year or two ago, and I’ve grown really attached to them. I made an ugly fish with big teeth! They provide a lot of great light, but since they’re so customizable, I’ve set them to change on a schedule:
9:30 AM (30 minutes before I start work): Be Productive

6:00 PM: Jungle

10:00 PM (or 11:00 PM on the weekends): Starlight

This helps provide visual signals when my day has changed. The moment the panels go from light blue to green, I know my work day is over. Since Nanoleaf supports HomeKit, I also have the panels turn off as part of the “good night” scene when I go to bed.
July 2024: Shortly after I published this post, I decided that weekends should be special – I wanted my office to have a different feel on Friday and Saturday evenings, and during the day Saturdays and Sundays. I added additional schedules with completely different color schemes, so I can fully relax on the weekends.
Also, I added a HomeKit scene that dims every light in my home office 10% further at midnight, so I can more easily wind down for bedtime. That’s worked very well.
Conclusion
If you’re working remotely, I hope this helps give you ideas on how you can use technology to have a better work / life balance. It’s certainly helped me!
